A Security fuzzer is a tool used by security professionals (and professional hackers ) to test a parameter of an application. Typical fuzzers test an application for buffer overflows, format string vulnerabilities, and error handling. More advanced fuzzers incorporate functionality to test for directory traversal attacks, command execution vulnerabilities, SQL Injection and Cross Site Scripting vulnerabilities. Web Vulnerability scanners typically perform all of this functionality, and can be considered an advanced fuzzer.
Implementations
A fuzzer is a program which injects automatically semi-random data into a program/stack and detect bugs.
The data-generation part is made of generators, and vulnerability identification relies on debugging tools. Generators usually use combinations of static fuzzing vectors (known-to-be-dangerous values), or totally random data. New generation fuzzers use genetic algorithms to link injected data and observed impact. Such tools are not public yet.
Attack types
A fuzzer would try combinations of attacks on:
- numbers (signed/unsigned integers/float...)
- chars (urls, command-line inputs)
- metadata : user-input text (id3 tag)
- pure binary sequences
A common approach to fuzzing is to define lists of "known-to-be-dangerous values" (fuzz vectors) for each type, and to inject them or recombinations.
- for integers: zero, possibly negative or very big numbers
- for chars: escaped, interpretable characters / instructions (ex: For SQL Requests, quotes / commands...)
- for binary: random ones
Please refer to OWASP's Fuzz Vector's resource[1] for real-life fuzzing vectors examples and methodology.
Protocols and file formats imply norms, which are sometimes blurry, very complicated or badly implemented : that's why developers sometimes mess up in the implementation process (because of time/cost constraints). That's why it can be interesting to take the opposite approach: take a norm, look at all mandatory features and constraints, and try all of them; forbidden/reserved values, linked parameters, field sizes. That would be conformance testing oriented fuzzing.
-
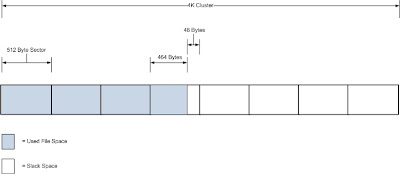
Slack space is a form of internal fragmentation, i.e. wasted space, on a hard disk. When a file is written to disk it’s stored at the “begin...
-
1. first you have to search or scan host that will be targeted 2. Start the the nessus, make sure the service has gone the way of open th...
-
1. Make sure windows xp is installed on Virtual Box 2. Make sure it is connected between the host and guest (BT5 and XP) 3. Cek ip guest t...
Subscribe to:
Post Comments (Atom)
Slack Space
Slack space is a form of internal fragmentation, i.e. wasted space, on a hard disk. When a file is written to disk it’s stored at the “begin...



No comments:
Post a Comment