Proxychain
Proxy chaining is merely connecting to more than one proxy and then to your intended destination. You can use as many proxy servers as you can or want. The more you have, the more anonymous you will be.
By using proxy chaining you will work by this way:
computer => proxy1 => proxy2 => ... => proxy X => web-site
Tor
Tor (The onion router) is a free software project and an open network that helps us defend against any type of traffic analysis, allowing us to navigate freely and anonymously. HTTP proxy cache polyp, which handles SOCKS4a, which prevents Firefox send DNS requests outside the Tor network, jeopardizing anonymity. It also speeds up navigation using the Tor network.
-
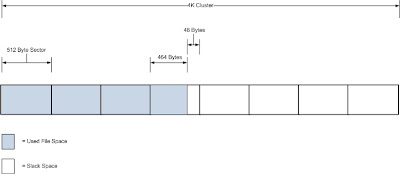
Slack space is a form of internal fragmentation, i.e. wasted space, on a hard disk. When a file is written to disk it’s stored at the “begin...
-
1. first you have to search or scan host that will be targeted 2. Start the the nessus, make sure the service has gone the way of open th...
-
1. Make sure windows xp is installed on Virtual Box 2. Make sure it is connected between the host and guest (BT5 and XP) 3. Cek ip guest t...
Subscribe to:
Post Comments (Atom)
Slack Space
Slack space is a form of internal fragmentation, i.e. wasted space, on a hard disk. When a file is written to disk it’s stored at the “begin...



No comments:
Post a Comment