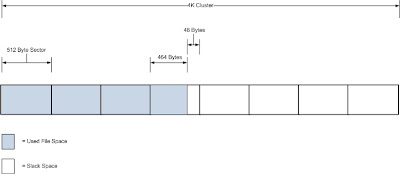
Slack space is a form of internal fragmentation, i.e. wasted space, on a hard disk. When a file is written to disk it’s stored at the “beginning” of the cluster. A cluster is defined as a collection of logically contiguous sectors and the smallest amount of disk space that can be allocated to hold a file. Rarely will there be an even match between the space available in a cluster (or collection of clusters for longer files) and the number of bytes in the file. Left over bytes in the cluster are unused, hence the name slack space.
-
Slack space is a form of internal fragmentation, i.e. wasted space, on a hard disk. When a file is written to disk it’s stored at the “begin...
-
1. first you have to search or scan host that will be targeted 2. Start the the nessus, make sure the service has gone the way of open th...
-
1. Make sure windows xp is installed on Virtual Box 2. Make sure it is connected between the host and guest (BT5 and XP) 3. Cek ip guest t...
3/18/12
The Unallocated Space
The unallocated space is simply defined as the area or space on the hard drive of the computer that is available to write data to.
The unallocated space is not viewable to the typical computer user and requires specialized computer forensic software to view and analyze. Unallocated space can contain deleted files or partially deleted files. When a file is deleted, the pointers to the file are removed, but the data remains in unallocated space until such time as the operating system stores another file in the same space, thereby over-writing the data.
The unallocated space is not viewable to the typical computer user and requires specialized computer forensic software to view and analyze. Unallocated space can contain deleted files or partially deleted files. When a file is deleted, the pointers to the file are removed, but the data remains in unallocated space until such time as the operating system stores another file in the same space, thereby over-writing the data.
File Structured and Examples
Basic File Structured
There are 6 basic file structure
1.Pile
2.Sequential File (SF)
3.Indexed SF
4.Indexed File (File berindeks majemuk)
5.Directed Hashed File
6.Multiring File
File access methods
• Some file systems provide different access methods that specify
ways the application will access data
• Sequential access
– Read bytes one at a time, in order
– This is the most common mode.
• Random access
– Random access given a block/byte #
– Examples: data set for demand paging, libraries, databases. . .
• Keyed/Indexed access
– FS contains an index to a particular field of each record in a file
– Apps can find a file based on value in that record (similar to DB)
– Can be considered a form of random access
There are 6 basic file structure
1.Pile
2.Sequential File (SF)
3.Indexed SF
4.Indexed File (File berindeks majemuk)
5.Directed Hashed File
6.Multiring File
File access methods
• Some file systems provide different access methods that specify
ways the application will access data
• Sequential access
– Read bytes one at a time, in order
– This is the most common mode.
• Random access
– Random access given a block/byte #
– Examples: data set for demand paging, libraries, databases. . .
• Keyed/Indexed access
– FS contains an index to a particular field of each record in a file
– Apps can find a file based on value in that record (similar to DB)
– Can be considered a form of random access
The Magic Number
In computer programming, the term magic number has multiple meanings. It could refer to one or more of the following:
- A constant numerical or text value used to identify a file format or protocol; for files, see List of file signatures
- Distinctive unique values that are unlikely to be mistaken for other meanings (e.g., Globally Unique Identifiers)
- Unique values with unexplained meaning or multiple occurrences which could (preferably) be replaced with named constants
3/15/12
File System Explanations
The file system is a system to find out how to store data from a specific file and file organization is used. The file system provides support that allows the programmer to access the file without any details concerning the storage characteristics and timing equipment. Change the file system file access statements to the instruction input / output low level.
Master Boot Record (MBR)
The Master Boot Record (MBR) is the information in the first sector of any hard disk or diskette that identifies how and where an operating system is located so that it can be boot (loaded) into the computer's main storage or random access memory. The Master Boot Record is also sometimes called the "partition sector" or the "master partition table" because it includes a table that locates each partition that the hard disk has been formatted into. In addition to this table, the MBR also includes a program that reads the boot sector record of the partition containing the operating system to be booted into RAM. In turn, that record contains a program that loads the rest of the operating system into RAM.
3/5/12
Web Attack Advanced on DVWA (File Upload)
Let's go on....
1. Sure the apache and mysql was started
2. Open DVWA on your browser http://127.0.0.1/dvwa
3. Setting your DVWA security to be high (i'm use file upload vuln)
1. Sure the apache and mysql was started
2. Open DVWA on your browser http://127.0.0.1/dvwa
3. Setting your DVWA security to be high (i'm use file upload vuln)
Subscribe to:
Comments (Atom)
Slack Space
Slack space is a form of internal fragmentation, i.e. wasted space, on a hard disk. When a file is written to disk it’s stored at the “begin...